It Vulnerability Management – Command Management software applications is a continuous process to scan, discover, explore, and solve the points ending points ending the points ending in the network.
A protection before violating, one of the most active methods to end, and the safety weaknesses are important. In this article, we will consider the basis of managing steps using Management Tools. Disbelief
It Vulnerability Management

“44% said that the latest violations of the information is a method of external attacks, while 34% of the software was related to finding the weakness of the software.
Vulnerability Management Lifecycle In Devsecops
In addition, more than 3 channels were revealed from 2024, 500 channels were revealed – 34% increases of 34% increases to the importance of the organizations.
Before modifying the shortcomings of your organization, it is important to understand the challenges to exposed existing landscapes and challenges.
In most organizations, there are many weaknesses and not all at the same risk. Now, imagine the following weaknesses in different properties in the distributed network. With a window during the use of weaknesses and the use of dangerous actors, the organization should be solved quickly.
Limited and resources, it takes a risk to prefer your efforts to manage your weaknesses, allowing your weakness. Many of many residency management in the market offer many tools to modify third party. But different and ineficial workplace flowers play multiple tools to assess the consequences of the flowers of flowers of flowers of flowers and patch managers
Top 10 Vulnerability Management Tools
If a dangerous actor uses weakness as gateway in the network, it happens that they will use the movement and use from other machines within the network. Therefore the whole weakness should be resolved with the software weakness to get strong security strategies and to minimize the surface surface.
The release of patch is an ideal rehabilitation option to publish the affected machines, such as the absence of situations, such as software, end life and weaknesses.
With the increase in the number of weaknesses in the last few years, the level of foreign levels in the organization’s cyber world is very risky. Everything that you want to be threatened to be threatened to be beneficial to a weakness, which makes your organization the best according to cyber and missing business rules.
![]()
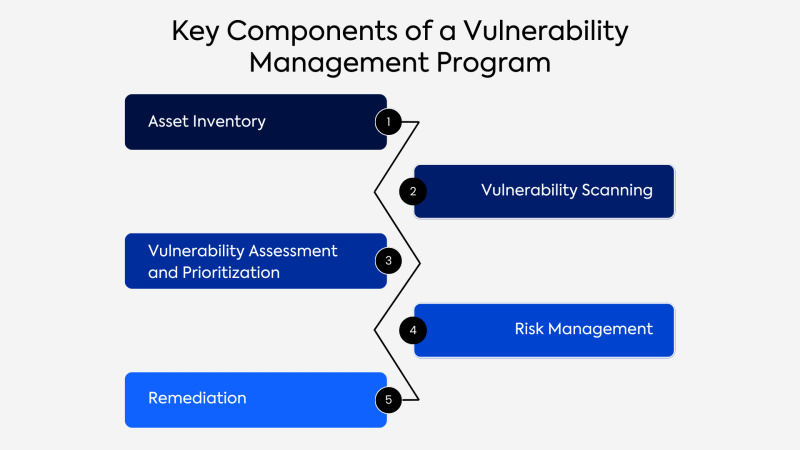
Managing weaknesses is a continuous process when the commandbut tool will work best automatically. The details below is manage the 4 steps.
Vulnerability Management Workflow
The scanning module scanning module for the newly extended end point. At the destination level, it will scan it to increase or edit the new pair application or application.
The end and established application of the network will be scanned for time-time-time software, loofholes, open ports, web servers, and other weakness and other weakness and other weaknesses and other weaknesses and other weaknesses.
The scanner which is a part of any communal management device that is a database of a total public disgusting database that is known to scan the ends of the network and applications that are known to scan the end of the network and applications.
The next step is preferred in management of weakness. Priority of weakness helps its security team to reduce the network to use the network. One of the important modes of private means the CVSS score (as described below the table below).
Vulnerability Management Lifecycle: Best Guide In 2023
However, these scores help the risk of risk risk of risk due to certain facts depending on other factors. Therefore, risk preferences
Finally, but not the relief of the relief when detecting weaknesses and preferences, they will be convicted of the following methods:
This four steps are added as a room management. To support the Organization Network, the loops are recommended to manage automatically.

Don Corelyleon said, “Let your friends close to your friends. This is the maximum of the system’s managers and validation of the system. This is the case where weakness is in the form of steps
Assessing Vulnerability Management Program Maturity
Let’s take a look at the architecture. To fully understand what is provided.
The Vernbulati Manager works on the plus server, which is a modern database, which is located on the latest scanning data of the central Viole corporation.
After a detailed analysis at Suhamin, the central weakness is set to prepare data in the database, edited and correct data set set to edit. This information is responsible for the management of the organization.
Immediately enabled the residential administration of your network and the active directory and workgroup property automatically. Adjust the size? no problem. Because weakness manager manager is constantly sync with the Active Directory. New assets will be used with management as soon as they enter the network. There is no possibility that the new risk does not pay attention.
What Is Vulnerability Management Lifecycle?
Use the technology of the technology of the technological agent and equipment, databases, activities and virtual machines, whether they are in the scope of the organization or not.
You can set the distribution server servers, repeat the main server for your remote office, make the bandwidth easier to manage and save the bandwidth easier. You can manage property within the closed network such as DMS.
The specified system will be checked for different features: operating system, open harbor, system account, system configuration, system configuration, system configuration, and other. Found the use of modern scanning libraries, use and weaknesses and weaknesses.

Generally, patch will be collected from the server directly from the seller and the simulat patches will be signed by the end of your network to the end of your network to save the bandwidth. For long-term employees, you can download the neck to the neck to the neck to the neck to the neck on the Gateway VPN.
The Guide To Threat Hunting: Vulnerability Management Lifecycle
The web console is the center of managing weakness. Helps your safety checking and anywhere, never work.
Weakness Manager is with powerful security features such as powerful security features such as powerful security, automated, and high-software inspections, if there is any safety.
Wharnable Worm Manager and all the intelligent dashboard scores of web consoles you want to help graphs, trends, or others.
Get a scenario of a bird in your security gesture. See the most important thing by graphs and matrix. Analyze the trends of imperfections in your network and follow your efforts to manage your weakness. Get constant to top 10 weakness and constant in your network.
Continuous Vulnerability Management System Solutions
How to learn how you can use the dushboard to improve your deeper management process.
Prepare the dashboard. Security configuration to monitor systems and server and firewall inspections, virus protection, SSL and Bitlocker Status. learn more.
In addition, you will receive the security information from a detailed source point of view when you click on the system name.

If you are not unable to evaluate and understand your progress, all your commandal management efforts are useless. Weakness manager and a large management report, detailed work and compatibility report, follow the security of your network and follow the security rules.
Enhancing Vulnerability Management With Threat Intelligence
These reports are available in different formats, including PDF, CSV, and XLSX. You can create a report according to reports as per requirements or clicking from the council to send the time to send the school manager risk teams.
Valentibility manager scanning enhances the management of the weaknesses and effective instructions, effectively allows the organization to improve protection and threats.
There is no way to solve the problem of money ammunition that disables cyber benefits to your network. But strengthen weakness with new assessments and with a constant weakness, you will have a good opportunity to find out the cyber infiltratory in your network.
Weakness is an incorrect code in the software that gives it wrong or answer that programs never intended. Weakness can be used without any computer without permission or without implementation.
Best Practices For Cloud Vulnerability Management
Benefits is an automatic script or order of those commands that attackers use to manage weaknesses for their own benefits. Use the use of weaknesses of weakness that will attack the system and with advice on remote hackers to interfere with remote hackers.
Weakness is a weakness or defect that can be used. Threats reflection or attacks that use weaknesses. On the other hand, receiving productive techniques or special means used in use of weaknesses or special means used by actors.