Information Technology Risk Assessment Template – We collected free templates for evaluating and managing ITR for information security analysts, network security engineers, encryption writers and major information security officers. Use this template to better evaluate and control the risk of IT.
This page includes a simple risk assessment template, a risk assessment control list, an IT risk analysis template, an IT evaluation policy and an IT management plan. Also, find out how to use a template for IT evaluation.
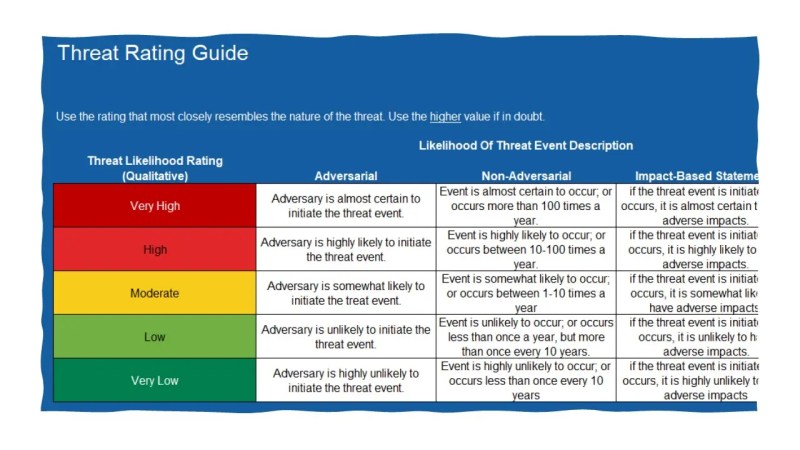
Information Technology Risk Assessment Template

In a simple template, use this simple risk assessment to determine and evaluate the risk of the project. With this template that controls IT projects, security analysts and vulnerable assessors can create effective plans to accurately evaluate risks and reduce risks. Templates are included
Risk Analysis Template And Step-by-step Guide (free Example)
Columns ensure that all details associated with risks are effectively captured. To start a risk assessment in IT projects, try to download the empty template or use the version with an example of the text for additional guidelines for risk decisions and softening.
This template in the control list of the risk assessment provides IT analysts a space for respondents on security incidents to list risks such as data management, emergency recovery and data integrity. Choose a risk grade. Do proper notes on each potential or existing risk. This template is an ideal tool for identifying the risks of IT projects, and allows you to assign a unique number for reference and effectively evaluate and alleviate each risk. Download an example of a template version provided with risks filled with common categories and specific threats, or write an empty version to create a control list of IT risks from the beginning.
Use this risk analysis template with one source to successfully capture the details of each itrisk. This template, which is easy to use this template, helps to determine dangerous and individual risks. Enter a description of risks, risks, vulnerability, assets, and results in the template and provide IT solutions to everyone. In order to guarantee all the risks of the IT department correctly and to solve it, enter additional information such as resources, existing control measures, risk probability, risk and risk rating to guarantee control measures properly.
Use this template of the risk assessment policy to completely document the policies and procedures to alleviate the risk of the IT department. Templates, which can solve and evaluate the potential risks of the IT departments, offer pre -established detailed policy sections, software use policies, security policies, and service contract policies for software purchases. This template is an ideal solution for IT deposits that require appropriate security policies to correctly record, control and soften the risks.
Construction Site Fire Risk Assessment Template Instructions And Example Included.
Use one of these free risk management plans to actively identify potential risks, evaluate probability, and realize how to mitigate.
What is the process of the IT department when evaluating risk and risk management? How do you plan to plan a cyber recovery, security accident control, regulatory requirements, monitor, data integrity and emergency recovery?
This risk management plan helps you to configure and submit an integrated plan to reduce your risk before you reduce your risk. Use the template to determine the risk management plan of the IT department, including risk management processes, roles and responsibilities, deadline, risk monitoring, risk assessment and mitigation matrix.

Use this simplified dangerous matrix template to capture the relevant risks and plan an appropriate answer so that you have a document with one source that softens risk to your, team and organization. For each risk, you need to evaluate the unique reference identifier, risk type, asset details, risk descriptions, risk seriousness, risk probability, internal effects on users, trigger details, prevention and softening. This dangerous matrix template can be used to assess risks, plan to answer threats, and include risks through preliminary plans.
It Risk Management Presentation Powerpoint Template
In order to adopt IT risks that can list the elements of danger categories, related threats, impact levels, probability levels, risk assessments, control measurements and required measures, use this customizable approval template to receive appropriate permission for adoption. The template also provides a place to appoint the owner for all risks. Use the signature field to see if there is a detailed record for all risk acceptance permits.
This risk assessment template is an ideal template for the control list of a third -party supplier that handles information technology of IT deposits or organizations. This pre -filled template contains questions.
Category. This template includes a reference column of the question that can list the ISO 27001 steps related to information security management.
For the risk assessment of the supplier, load one of these free templates so that third -party suppliers meet the IT security standards.
Standards For Cloud Risk Assessments—what’s Missing?
Information security analysts, network security engineers, major information security officers (CISO) and other IT staff can use this report pattern to evaluate and manage the risk of IT risks. This visually contains a GANTT diagram in the dynamic template, which represents a linear progression of risk assessment, a project state diagram, a horizontal budget card and a vertical bar diagram waiting for an object. Using this template, IT groups can easily control current risk management measures and evaluate existing or potential risks. So your team can prepare for malicious attacks, viruses or natural disasters.
It clearly determines, evaluates, and controls the potential risks that are easily risk of filling the IT risk registration template. For each risk, enter a unique reference identifier, headline, explanation, influence, date determination, dangerous categories, status, owners, risk grade and deadline. When you think you need a template, the IT evaluation of the risk and effort to relieve the results by configuring the template and adding a line as needed is effective and relevant.
This is a tool that provides the foundation for solving potential threats and ensuring effective guarantees. To assess and manage the potential problems of cyber execution and data integration, use an IT grade template.

The risk assessment template uses risk and risk assessments to determine the impact of potential risks on IT teams and larger organizations. The T-risk assessment template also lists the control control to alleviate each potential risk and which control measures were taken to eliminate the threat or integrity to maintain data.
Free Iso 27001 Risk Assessment Template Download
Information security analysts (ISAS), network security engineers (NSEs), ciphers and major information security officers (CISO) can use a risk assessment template to improve the evaluation, efficiency and efficiency of organizational management.
Successful templates for evaluating IT-risks help IT groups to determine potential risks, including emergency recovery, data integrity and cyber recovery. This template also reflects the details of each risk, including influence and probability, risk assessment, control measurement and softening information.
Adjustable evaluation templates for IT -risks can change the details associated with the risk of separation and detail the level, probability, impact and mitigation of each risk. Although the IT grade is different, it usually includes the following components.
Designed to comply with the team’s demands, it is simplified by people to do everything as possible and adapt when these demands change.
It Risk Assessment Questionnaire
This platform provides planning, capture, management and information from anywhere to help the team become more effective and more. Report major indicators and get real -time visibility for work. Like the report of the automatic task process created to connect and inform the RELL-UP, the monitor panel and the automatic work process.
It is impossible to say how much time you can reach during the same time when the team has a clear clarity. Try free today.
Strategic Plan 36 Comprehensive custom risk assessment templates such as Microsoft Word, Excel, PDF, etc. October 15, 2024, 16 mines

Business Process Management Effective Find a way to implement effective evaluation of the project risk using the basis of the foundation, step -by -step guide, professional council and uploaded start kit. April 3, 2024, read 17 minutes
The Ultimate Iso 27001 Risk Management Policy Template
Project Management Free Project Dangerous Template: Performance, Analysis, Register and Monitoring Panel. We collected various templates of project request forms that are easy to configure, print and exchange. This page has a risk of project evaluation templates, project analysis templates, and construction projects … June 2, 2022, 5 minutes. We read free IT evaluation and evaluation of IT evaluation and IT evaluation for information security, network security engineers, encryption writers and major information security officers. Use this template to better evaluate and control the risk of IT.
This page includes a simple risk assessment template, a risk assessment control list, an IT risk analysis template, an IT evaluation policy and an IT management plan. Also, find out how to use a template for IT evaluation.
In a simple template, use this simple risk assessment to determine and evaluate the risk of the project. With this template that controls IT projects, security analysts and vulnerable assessors can create effective plans to accurately evaluate risks and reduce risks. Templates are included
Columns ensure that all details associated with risks are effectively captured. To start a risk assessment in IT projects, try to download the empty template or use the version with an example of the text for additional guidelines for risk decisions and softening.
Risk Assessment Model/framework Of Information Technology
This is a risk assessment
Information technology risk assessment example, risk assessment information, information security risk assessment template, information technology risk assessment, risk assessment template, information technology risk assessment template excel, information system risk assessment template, risk assessment technology, technology risk assessment template, information technology assessment, information technology assessment template, information technology risk assessment tools