It Vulnerability Management Process – The contercerafcial guintations is the secret protection process against the number of cyber in our SYBER period in our database. Only 2023 more than 30,000 30,000 were noted, with an increase in the 42% and emphasized the urgent need for printing plans. As opponents, including socially supported groups, such as Aprus, are quick to use these security defects, organizations should accept control information from being unduly.
The Hazard Administration was aimed at solving the IT infrastructure infrastructure. The program begins to see potential defects with the supervision monitoring. After identifying security weakers, they are assessed in accordance with potential impacts and are more likely to use, prepare preparation. The final phases include the implementation of appropriate corrections and implementation of reporting and documents, for protecting them against new threats.
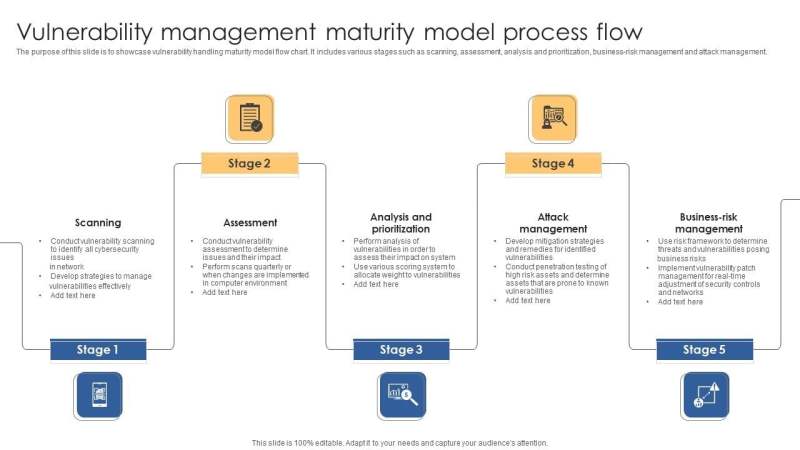
It Vulnerability Management Process

In terms of the six of the following phases of the above phases, security groups can build strong security, minimizing the risk of breaking.
Strengthen Your Company’s Cyber Security With Vulnerability Management
The first step includes comprehensive identification of all assets on the network that may contain security defects. To achieve a significant understanding of the organization The solution needed for verification, thus preventing potential infections.
To ensure that security teams collect all relevant data to find the threat, they can rely on the soce scripive. The solution allows organizations that strengthen the weEM’s attitude uses the prescribed plan to develop threats and solve a high-risk alarm and alassied at a time of threats to eliminate the risk.
After catalogs and distinguish all items, these assets are subject to scanning test and submit to vulnerable persons. This level involves an assessment of the problems identified to determine the potential impact on the position of the organization. Roads such as the login test and the accident model are usually used to repeat potentially and evaluated the risk of weakness.
It is because time that lasts growing the new GAPS number found in popular software. Affecting the use of the use of the situation is one of the most common circumstances. The so Soon Soons in Rint runs a large algoroitm library Algoroitm, a 5,000 SLIT period to find out the use of suffering.
Vulnerability Management: Processes And Tools
After identifying security posts, they should be evaluated and involved in size, potential impacts and use. Normally, SOS teams use the following methods at this level:
This stage is necessary to choose the construction of equipment and focus on efforts in important threats. To help protect the success of the effluence of Intel threats, advertising advertising ads matching algorithms, Pvit, Ck and reduce.
When security parties with the main list of security defects, the next step is to resolve potential threats. There are three ways to solve:

To ensure the success of the intervention and reducing, SOS teams run notes and testing for clothing. This audit focuses on the guarantee that all posts are solved and if there are no new problems from roads.
Vulnerability Management Guide: Systems & Processes
In addition to this emphasis, the security team also conducts a wide range of network study. This includes identification of all new posts that may be required from the last scan, to assess the importance of high elimination and record some changes that may require one intervention. The results of these activities are the key use of the next life cycle.
In the final phase, security groups record the results of the latest cycle, detailing the vacancies, repairs and outcomes. These detailed reports were then distributed to important stakeholders, such as management, asset managers and legal officials.
In addition, the security team assesses a comprehensive assessment of the cycle. This includes the management of the most important symptoms, such as the MTTD), the maximum response period (MTTR), the number of posts and directions. Tracking these cites at time to establish a barrier management system and identifies areas that need improvement. Recognition that each cycle is used for improve and improve future efforts.
Carefully by following these levels, organizations may adopt the Cyber Safety location, identified effectively and facing potential spaces before being used by difficult sectors.
Efficient Vulnerability Management With Limited Resources
The implementation of the management cycle of life is improving cybernetic district plan, strengthening its asset protection and maintain protection. The life cycle provides a set of resources and contributions and safe and well-known place.
Earnings based on the basis of data related to data. Regular scanning and negligence while prevents invasion in crime programs. This allows security groups to find and evaluate potential weaknesses, delivering important data for the growth and decision-making. This accuracy correctly allows you to adjust security measures to solve certain leopholes by safety, and therefore improves the risk reduction.
A valid cybernetic case. Create strong management systems that form the problem-solving organizations and reduce your keys before the invaders can use them. This working attitude reduces the chance of attacking success, reduce potential damage and increase the general safety attitude of the organization. Before you also honors and identify safety blindness that can affect the safety of the organization, organizations can save strong assets, keeping their clothing and complex data.

The allocation of appropriate equipment. Identifying and resistant to help organizations reduce the rest time of the program and protect their data. To improve the process of consideration the management management reduces the return time after the events. The integration of a special life control and security plan allows to be distributed and money by establishing the priorities of safety and effect. This ensures that human resources focus focuses on the most important problems, leading to good governance and effective use.
How To Secure Thousands Of Websites With A Small Security Team
The route set for security measures. The trend management course contains the usual protection teams for the normal process of operating and repairing items, to ensure continuous improvement of security measures. This coordinated approach provides reliable results, allowing organizations to operate automatically and expand the value of investment. Continuous verification helps to maintain a solid security attitude and practice from remaining in the vyber security solvents.
For decades, business jokes are an involvement, and security personnel / work often has opposite ideas. Organizations remain facing the challenge of measurable between the quick implementation and the correct testing. The implementation of the packages quickly reduces the window of the potential for invaders, but increasing the risk of effective interventions due to adequate assessment. Nist published 800-40rr4, Guidelines for Business Technology, renovation technology, aims to use this software related to the use of CO4.
This guide serves as a comprehensive creative book and implement a solid business management system. It emphasizes a stricted approach to emphasizing materials and evaluating the empowerment of unforeseen unrequivilization to identify and understand potential impacts. This guide emphasizes the importance of the importance of assets and security equipment successfully achieves the effective and effective program.
Nist SP 800-40r 4 provides as a necessary maintenance factor system to facilitate the maintenance technology, bringing them as a reasonable organization cost to complete their commission. Continues with joint challenges to regulate business pieces and suggests the construction of a comprehensive strategic improvement plan while increasing risk reduction. Implementation of the prevention savings is essential to preventing the announcement, data breach, interruption and other negative events.
Navigating Vulnerability Management
The special NIRD record describes the need for priority priorities based on a coordinated risk assessment, which leads to effectiveness and effectiveness. This ensures the implementation of the targets, taking into account the maintenance plans and to be different to deal with care and posts.
In addition, the guide emphasizes the importance of ensuring and monitoring the operation of the patch, supported by a strong and continuous information, which remain increasingly increasingly.
To take into account these factors, the publication provides depputual guides, to provide the identity of valuable values and practical indicators that allow cyberrinetice organizations to improve the threat.

In the event of a continuity of the assault, it is essential to ongoing organizations for future governance, facilitating efficiency and integrating opportunities to appear, test and reference. Based on the sosproft platform in the cybernetic sector in the globereet of the globe, the trustee that is a potential to protect the vicious risk.
What Is Vulnerability Management Process?
Join SOF PRIM to be found as a coding platform to improve the appearance of threats to your company. To help you start and run the price immediately, the book is now with Specialists.
This website uses cookies (small files stored by web browser on user device) to improve
Vulnerability management process template, vulnerability management process document, vulnerability management process steps, it vulnerability management, vulnerability management process flow chart, vulnerability remediation process, vulnerability assessment process, vulnerability scanning process, itil vulnerability management process, vulnerability management process, vulnerability management remediation process, vulnerability and patch management process