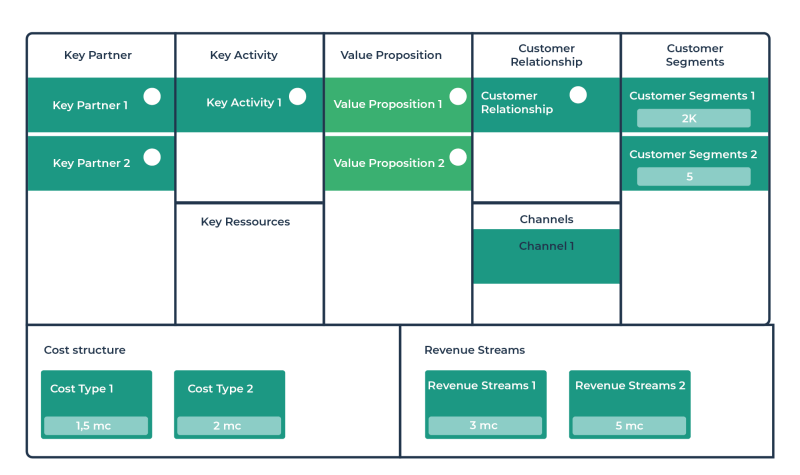
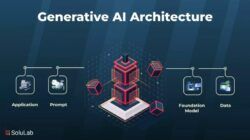
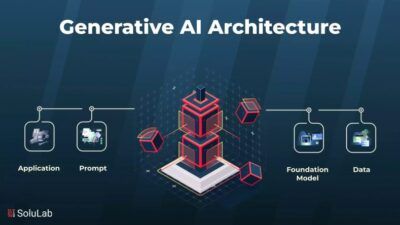
Technology Architecture In Togaf – Business structures (including security plans) is all about changing business practices to recognize business goals, people are a combination of procedures, people and sciences). One of the key features of trading plans is the security of information and how to travel. For a very long time, information security is considered separate discipline, transferred with trade practices and business operations.
The security process is the nature of the organization’s organization organization of the soft and physical organization that uses a cooperation in order to succeed and keep security danger with. He is a driver and a tutor of secure, secure, secure, secure, secure and dealing with danger.
Technology Architecture In Togaf

However, business security missiti is not exposed to isolate ourselves. As part of the business, builds in trade knowledge that is already available in business designs, and produces the influencing information part of the business plans. This is whether the doors associated with and works with the security road in the order of trade plans. Eventually, in making sure this time saves costs and increases to work properly in comparison with security. To achieve these purposes of security and business activities need to speak one language. The language is presented in this guide, which describes the method of merging safety and danger into a business trade practice. Provides guidelines for security agents and business activities in practical activities and togaf
Togaf Business Architecture In A Nutshell
Figure 1 includes this guidance. Indicates how training facilities and compositions of trade-related opinions and risk is used in the information system (ISM) and systematic materials. These concepts are listed in the unit column, making a list of fundamental concepts and improve the status of Togaf. The ideas with printing in numbers increases in the form of confrontation and delivery by ism or erm.
These new content perform the protection tasks in a lot of togaf [1] to a higher mind level. This project is to explain how togaf method and togof form can be adopted to use the preparation of safety and accident.
This method is carried in business and supports two-processing relationships: ISM and ERM. This responsibility gains understanding of the securities of security and various style functions in a variety of togaf (ADM) strategies. Business mass contributes to justify security features.
This approach is required for a lot of other security security security guidance required. This guide provides the basis of that task. Using a common basis this provides an unreasonable and practical way of working in.
Enterprise Architecture Best Practices In Large Corporations
The usual risk stagaf system speaks a lot about being in danger of invention. This is the only form of danger. EMOR EBONE, as shown in this guide as part of the business security plans, is very widespread. This includes business, system, information, information, privacy, privacy and danger of the invention change, among other categories.
This guide describes Erm orm’s idea and whether to combine them with togof conditions. In particular, this task focuses on all accidental areas – put the business faces in accordance with the overall processing ability. It is believed that by drawing the risks of working on the floor than the delivery of business products, equipment, quality, and successful work products will improve and improve.
Business trade mutations have a perceived perception: Bad effects are kept in an acceptable position and fine opportunities abused. Trade-run mode is the most important security system: business drivers give the meaning of risk test; They explain whether to comply with any management method is needed, we need to justify security measures.
This guide is clearly viewed in the sake of a good episode. It is written for experts expected to use good habits and are ready to read and take a talk in work. As with vessels, risk work changes and get better. Central to merm is a very clear definition of the term “accident”. In the past 15 years the system has produced professional definitions in accordance with the concept, physical exercise in good mode. The Danger Description is included with unique international standards such as ISO 31000: 2009
Download The Introduction To The Togaf Standard, 10th Edition
There is a difference between a common description of “harm” and experts of experts in danger. Within professional work “accident” is defined as “
“. For many medical security doctors, this explanation may feel uncomfortable in their discipline, discipline, accident is considered to be attached to the threat.
When this guide preaches the valuable ideas of the redesign, the danger’s explanation allows the use of the time in question just as bad; For example, in a professional information area of information information for information property, where unknown is not at all the result.
First of all, the integration is not a matter of choosing checks from the list. We encourage self-defense, to manage a reliable, trusted, reliable, safe, safe and danger. To do this, business design in business confirms that the hard cooperation of Adm is reached with EMM and EMM process. Thus, many concepts of this guidelines lead to things that need to stop sufficient security.
Applying Enterprise Architecture Rightly
However, the performance security plan is also part of ornamental. In the invention level, security control is collected security services. Security service can see as a vegetable construction block (abb). In case of Togaf, Abbs are specific plans and guide the development of solution blocks (sbbs). This can apply to all the plans of the Togaf Domain: Business, Data, Application and Technology. Similarly, security services capture security requirements and guidance to guide the development of services and other parts.
The planning planning plan, updated in Phase C (information planning plans) of Togan ADM. Protection Protection Protection Provides the current definition of security services.
To support security manufacturers in the form and use of security services, in the security list is required. For security plans, security protection process is a registration supporting a vivid part of the Sabsa formula. Unlike existing variables with requirements, the security listings describe safety restrictions that are verifying the protection. This method of these designs allows to meet the best in technical security system that has learned.

The usual method that provides a means of using security agency advice and enabling work. One of the provisions of the security issues is that it gives a standard expression of the sentences and a defense administrative plan that allows the best cooperation between the parties involved. This article is ready to describe differences between the togaf and planning planning plans / design models (SEF). Are you interested in understanding how these mines can be merged? This article provides a lot of knowledge of these topics without going to a very serious stupidity with many physical things.
Mdg Technology For Togaf
Togaf is a type of business format involving many agnotic variables, which includes multiple areas added in the schedule, clouds and science and science.
On the other hand, the clouds speak loudly by providing good practices, guides and plans and plans and plans and plans and plans and plans and plans and plans and plans and plans and plans and plans and plans and plans and plans and plans and plans and plans and plans and plans and plans and plans of plans and plans for the planning and planning and planning and planning and the planning and the planning and the planning and the planning and the planning and the planning and themes and themes and themes and plans directly with respect, by emphasizing the details of a number of grazing.
Surely there are replications and depression between these two designs, and we can examine this more than this.
“Business business minutes (of) is a practice of analyzing, planning, designing and inserting a solution to a business policy.” – opengroup
Enterprise Architecture, Togaf 10 & Enterprise Agility
Accepting business activity can help businesses help businesses to facilitate their methods to simplify the development strategies, and always reminds your persecution.
By setting the first measurements and improves the design of the designs, organizations can satisfy quickly and improve their situation.
Business decorations can support organizational changes, makes it easy to evaluate the designs form and give feedback to be outside them.
The Togaf® program is evaluated and maintained by members of the open group, working for forum. The main development of Togan Version 1 in 1995 was based on the planning planning planning plan (TAFIM), generated by the Department of Security (DOD). – open group
Mdg Technology For Togaf
It is good to influence directly in business transactions for all major businesses. 80% of Dow Jones